Centos7 安装 InConnect 客户端
Centos 环境
[root@centos-linux ~]# cat /etc/redhat-release
CentOS Linux release 7.4.1708 (Core) 1. 安装依赖环境
1. 1 通过yum 安装 openssl 和 openssl-devel 模块[root@centos-linux ~]# yum -y install openssl openssl-devel
1.2 安装 lzo lzo-devel[root@centos-linux ~]# yum -y install lzo lzo-devel
1.3 rpm命令检查安装情况:[root@centos-linux ~]# rpm -qa | grep lzo lzo-devel-2.06-8.el7.x86_64 lzo-minilzo-2.06-8.el7.x86_64 lzo-2.06-8.el7.x86_64 [root@centos-linux ~]# rpm -qa | grep openssl openssl-libs-1.0.2k-16.el7_6.1.x86_64 openssl-1.0.2k-16.el7_6.1.x86_64 openssl-devel-1.0.2k-16.el7_6.1.x86_64 [root@centos-linux ~]#2. 安装InConnect 所用的客户端 OpenVPN
[root@centos-linux /]# yum -y install openvpn easy-rsa
3. 下载配置文件,并导入到Centos 系统的 /etc/openvpn/client 文件文件夹
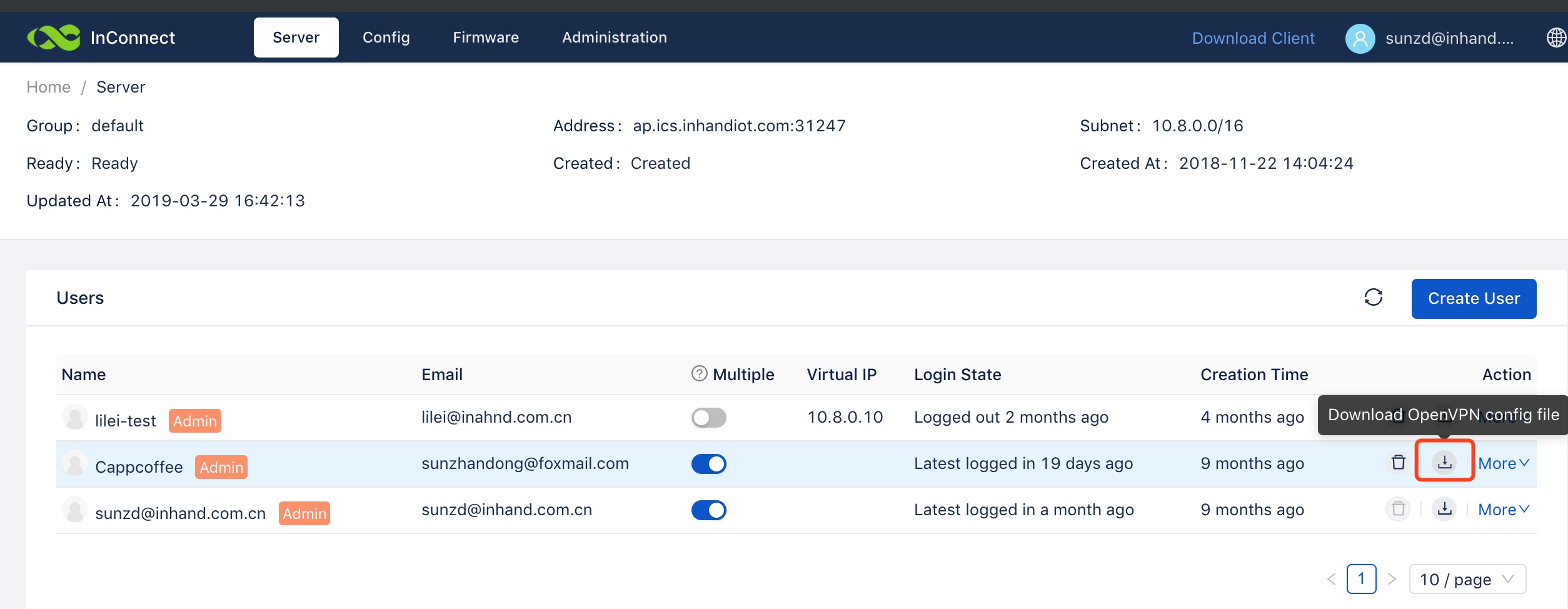
ps: 我登陆服务器是使用的CRT,使用ssh传输文件得安装lrzsz工具,通过rz 命令从本机将文件传给Centos系统下。[root@centos-linux client]# yum install lrzsz [root@centos-linux client]# cd /etc/openvpn/client/ [root@centos-linux client]# rz配置文件被成功上传
[root@centos-linux client]# ls
sunzhandong@foxmail.com.ovpn
4. 启动OpenVPN 客户端[root@centos-linux client]# openvpn --daemon --config sunzhandong@foxmail.com.ovpn --log-append /var/log/openvpn.log
⚠️ 配置文件为 sunzhandong@foxmail.com.ovpn 是本次测试使用的,请在命令中替换。
将上述命令加到里开机启动。/etc/rc.local参数解释:
- daemon:openvpn以daemon方式启动。
- cd dir:配置文件的目录,openvpn初始化前,先切换到此目录。
- config file:客户端配置文件的路径。
- log-append file:日志文件路径,如果文件不存在会自动创建。
[root@centos-linux client]# cat /var/log/openvpn.log Mon Aug 12 16:52:17 2019 OpenVPN 2.4.7 x86_64-redhat-linux-gnu [Fedora EPEL patched] [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Feb 20 2019 Mon Aug 12 16:52:17 2019 library versions: OpenSSL 1.0.2k-fips 26 Jan 2017, LZO 2.06 Mon Aug 12 16:52:31 2019 ERROR: Failed retrieving username or password Mon Aug 12 16:52:31 2019 Exiting due to fatal error Mon Aug 12 16:55:49 2019 OpenVPN 2.4.7 x86_64-redhat-linux-gnu [Fedora EPEL patched] [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Feb 20 2019 Mon Aug 12 16:55:49 2019 library versions: OpenSSL 1.0.2k-fips 26 Jan 2017, LZO 2.06 Mon Aug 12 16:55:49 2019 WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info. Mon Aug 12 16:55:55 2019 TCP/UDP: Preserving recently used remote address: [AF_INET]54.222.145.115:31247 Mon Aug 12 16:55:55 2019 Socket Buffers: R=[212992->212992] S=[212992->212992] Mon Aug 12 16:55:55 2019 UDP link local: (not bound) Mon Aug 12 16:55:55 2019 UDP link remote: [AF_INET]54.222.145.115:31247 Mon Aug 12 16:55:55 2019 TLS: Initial packet from [AF_INET]54.222.145.115:31247, sid=d52be281 825a6a96 Mon Aug 12 16:55:55 2019 VERIFY OK: depth=1, CN=InHand Networks InVPN Server Mon Aug 12 16:55:55 2019 VERIFY OK: depth=0, O=inhand networks, OU=inhand networks, CN=5bf646e15ffb44000100000e Mon Aug 12 16:55:55 2019 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA Mon Aug 12 16:55:55 2019 [5bf646e15ffb44000100000e] Peer Connection Initiated with [AF_INET]54.222.145.115:31247 Mon Aug 12 16:55:56 2019 SENT CONTROL [5bf646e15ffb44000100000e]: 'PUSH_REQUEST' (status=1) Mon Aug 12 16:55:56 2019 PUSH: Received control message: 'PUSH_REPLY,route 10.8.0.0 255.255.0.0,route-gateway 10.8.0.1,topology subnet,ping 40,ping-restart 120,ifconfig 10.8.1.1 255.255.254.0,peer-id 3,cipher AES-256-GCM' Mon Aug 12 16:55:56 2019 OPTIONS IMPORT: timers and/or timeouts modified Mon Aug 12 16:55:56 2019 OPTIONS IMPORT: --ifconfig/up options modified Mon Aug 12 16:55:56 2019 OPTIONS IMPORT: route options modified Mon Aug 12 16:55:56 2019 OPTIONS IMPORT: route-related options modified Mon Aug 12 16:55:56 2019 OPTIONS IMPORT: peer-id set Mon Aug 12 16:55:56 2019 OPTIONS IMPORT: adjusting link_mtu to 1625 Mon Aug 12 16:55:56 2019 OPTIONS IMPORT: data channel crypto options modified Mon Aug 12 16:55:56 2019 Data Channel: using negotiated cipher 'AES-256-GCM' Mon Aug 12 16:55:56 2019 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Mon Aug 12 16:55:56 2019 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Mon Aug 12 16:55:56 2019 ROUTE_GATEWAY 10.1.1.1/255.255.255.0 IFACE=eth0 HWADDR=00:1c:42:28:04:52 Mon Aug 12 16:55:56 2019 TUN/TAP device tun1 opened Mon Aug 12 16:55:56 2019 TUN/TAP TX queue length set to 100 Mon Aug 12 16:55:56 2019 /sbin/ip link set dev tun1 up mtu 1500 Mon Aug 12 16:55:56 2019 /sbin/ip addr add dev tun1 10.8.1.1/23 broadcast 10.8.1.255 Mon Aug 12 16:55:56 2019 /sbin/ip route add 10.8.0.0/16 via 10.8.0.1 Mon Aug 12 16:55:56 2019 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Mon Aug 12 16:55:56 2019 Initialization Sequence CompletedCentos 路由表
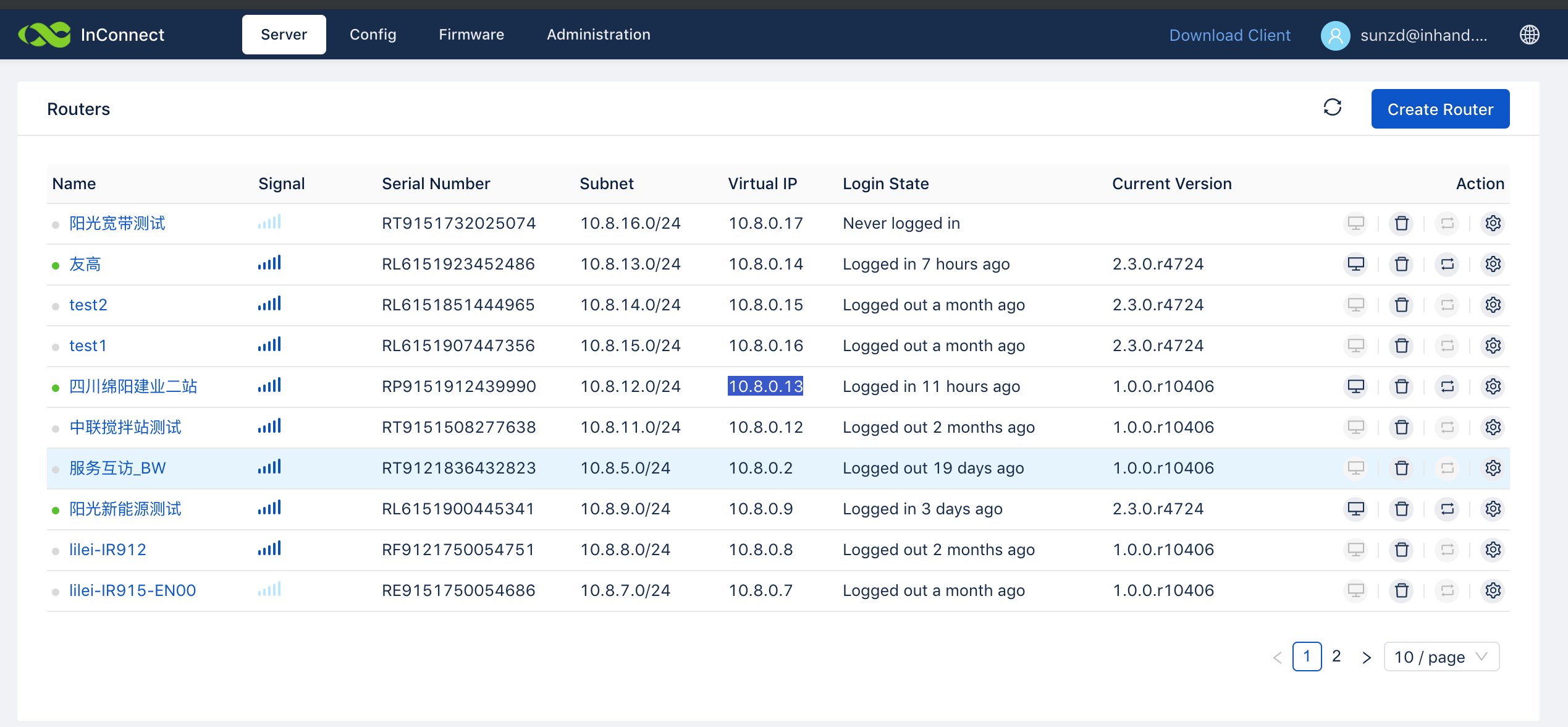
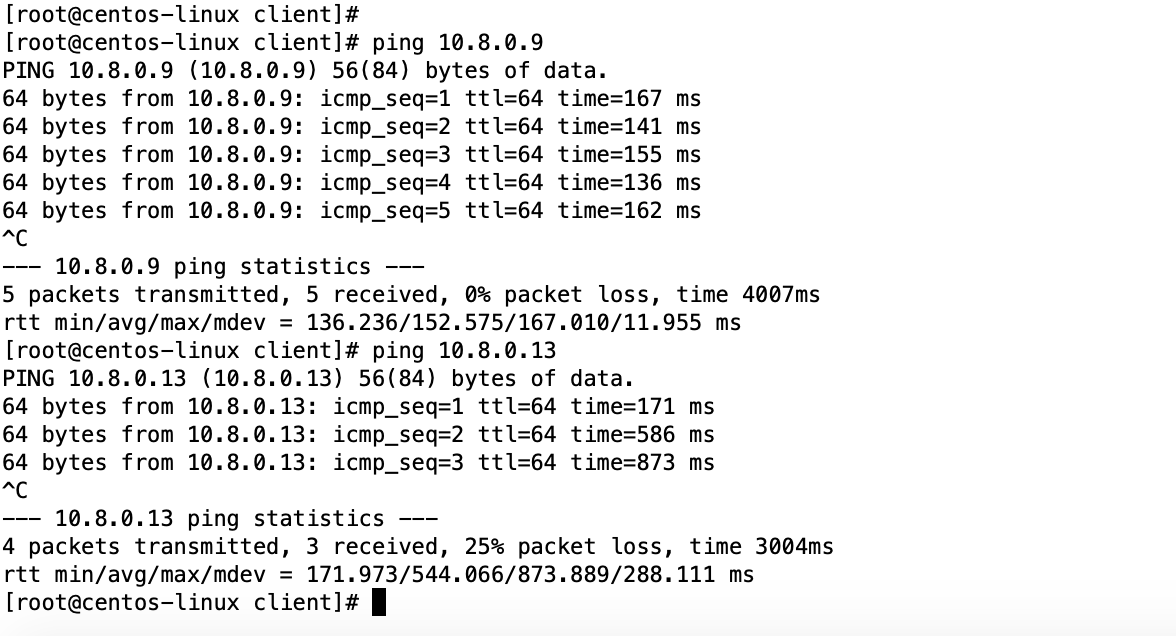
[root@centos-linux client]# route Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface default gateway 0.0.0.0 UG 100 0 0 eth0 10.1.1.0 0.0.0.0 255.255.255.0 U 100 0 0 eth0 10.8.0.0 0.0.0.0 255.255.254.0 U 0 0 0 tun1 10.8.0.0 10.8.0.1 255.255.0.0 UG 0 0 0 tun1 [root@centos-linux client]#Centos ping 下图路由器IP地址: